In this article, we will tell you how crypto hackers are doing cryptocurrency theft using fake phishing websites.
A cryptocurrency phishing scam is a type of computer hacking that involves tricking victims into giving up their private keys or personal information. The attacker typically masquerades as a legitimate entity or person to gain the trust of the victim.
This form of fraud can be used in order to steal cryptocurrency (such as Bitcoin and Ethereum) from users who believe that they are sending funds to a trusted party when in reality there are no network delays or checks.
Once the victim has been scammed, the crypto hacker then uses their information to steal their cryptocurrency funds. This attack is referred to as a “cold wallet hack” or a “wallet transaction.” It involves sending just enough funds to impersonate the victim, putting them on edge, and following that up with a viral email claiming their account has been hacked.
The Australian cryptocurrency market is being victimized by fake websites imitating popular crypto services.
Fake websites mimicking popular crypto services are fooling Australian cryptocurrency investors. Among other investors across the globe, Netskope Threat Research Engineer Gustavo Palazolo talks about a rising global cryptocurrency ruse.
As he explained, crypto hackers steal crypto funds by using fake websites that resemble popular crypto exchanges and wallets.
In addition to their apparent legitimacy, scam sites make use of search engine optimization (SEO).
Cryptocurrency wallets and accounts have been stolen from Coinbase, MetaMask, Kraken, and Gemini by hackers using Google Sites and Microsoft Azure Web App.
Further, they are adding resources to improve these phishing pages’ Google ranking, so they appear at the top of the list when people search for crypto exchanges.
“When victims attempt to log in or import an existing wallet, they are presented with a phishing page that asks for login or wallet information, which crypto hackers uses for cryptocurrency theft. Additionally, attackers attempt to contact victims through live web chat on these fake pages, to gather additional data that can be used to steal crypto funds.
As a result of social engineering attacks, known as ‘social engineering, malicious links or documents are being spread using search engines such as Google and Bing.
According to Netskope Threat Labs’ research, there has been a sharp increase in PDF files that are downloaded from popular search engines and used as phishing and scam mailers,” Mr. Palazolo said.
Crypto Traders in Australia are at risk
It is estimated that 17 percent of Australians own cryptocurrency, which means that Australians are not immune from the risks associated with cryptocurrencies.
It has been proven that these techniques work equally well across the globe, he stated.
As with other regionalized versions of the search engine, the fake pages listed in this study appear in results on www.google.com.au as well. Therefore, these phishing pages target victims all over the world.”
The researcher found that Binance, Coinbase, Crypto.com, Kraken, and Gate.io are all actively phished in Australia.
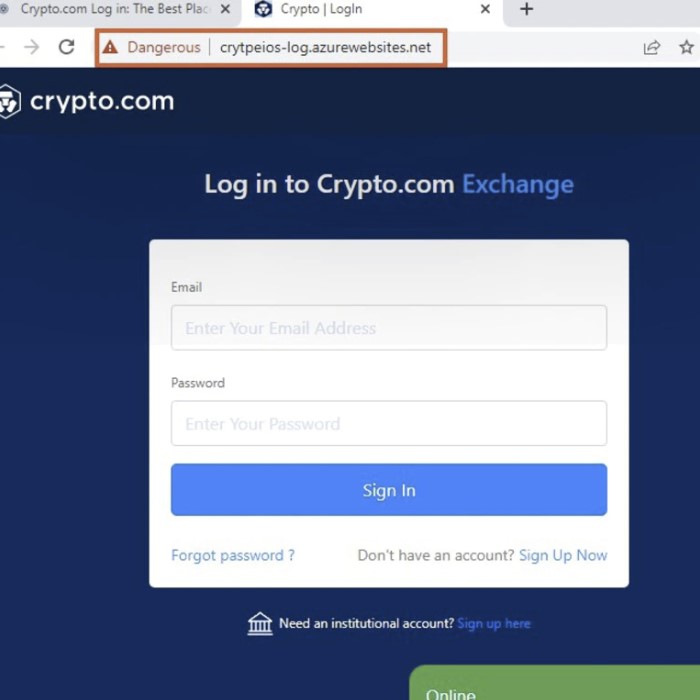
Sites under attack
As a result of the phishing campaign, the attackers in charge have proven to be resilient to countermeasures, according to Mr Palazolo.
“The attacker is taking steps to keep the operation online,” he said, adding that most of the URLs we found in August are still active.
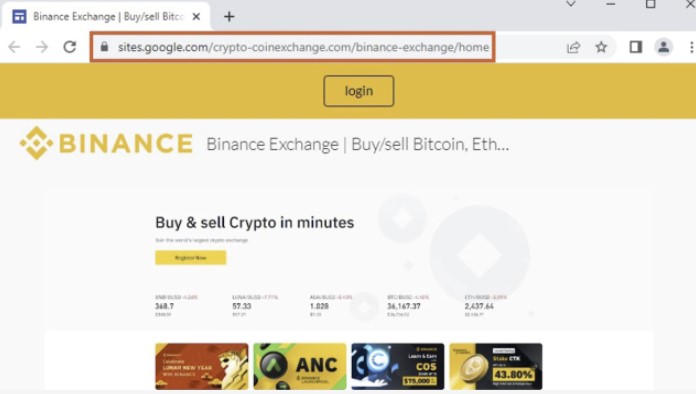
Aside from finding new phishing pages with the same targets, we also discovered phishing pages mimicking Binance, Crypto.com, Gate.io, KuCoin, PancakeSwap, and Shakepay.”
Phishers target the following crypto exchanges and wallets:
• MetaMask
• Coinbase
• Gemini
• KuCoin
• Crypto.com
• Binance
• Pancake Sway
• Kraken
• Gate.io
• Shakeplay
How cryptocurrency theft work
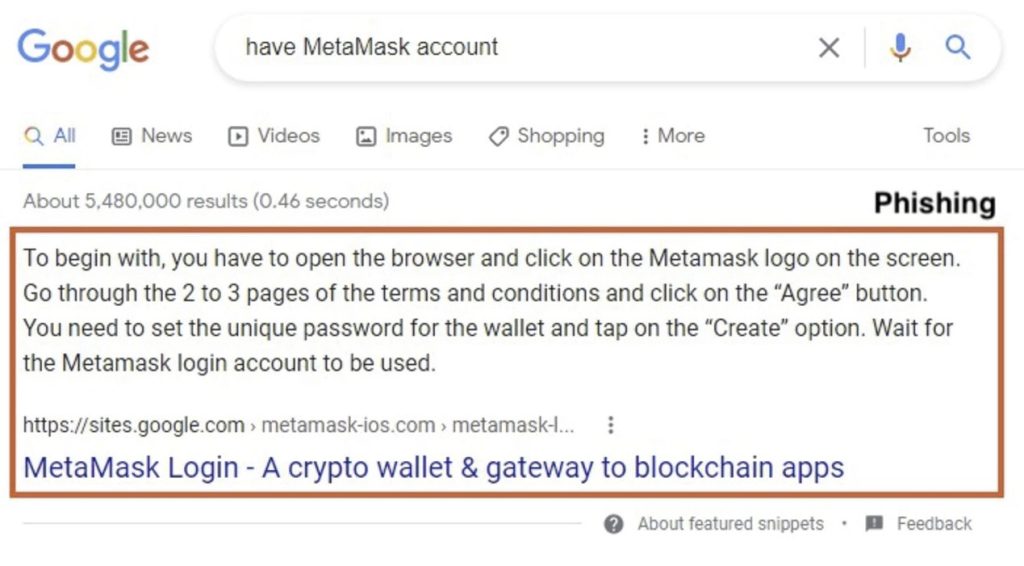
A phishing page is displayed first if the victim uses specific keywords to search for a cryptocurrency website (e.g. “having a MetaMask account”).
In addition to mimicking an original website, the phishing page contains several SEO elements. By clicking on links within the page, the victim is redirected to another phishing website.
On the second phishing page, the attacker attempts to steal sensitive information, such as the password for a cryptocurrency account or the secret recovery phrase.
Lastly, the attacker will attempt to steal more sensitive information via a live web chat with the victim.
Cryptocurrency security
In the upcoming months, Palazolo believes attackers will continue to use this method, as fake pages are very easy to reproduce after they are taken down.
He warned that attackers could easily continue their operations.
Direct navigation to your provider is the key to avoiding dodgy sites.
“We recommend that individuals never enter or give login information after clicking a link,” he said.
Whenever you are trying to log in, always navigate directly to the website.
“This is especially true when it comes to financial transactions. To access their accounts, individuals should also use multi-factor authentication, which combines several authentication methods.
Authenticators can generate passwords and verification codes via mobile devices, such as an app on a smartphone.
“Organizations must use a secure web gateway capable of detecting and blocking phishing in real-time.”
Via this site

